Since OpenVPN isn’t too chatty about failures in its default configuration, this took me a couple of tries to get right. Hopefully this post can save you some of the time I wasted.
In the following example, I’m assuming you already have a Raspberry Pi, running Raspbian and that you can access it over the local network. From the snippets below, change the example ip 192.168.3.14, to the ip of your local device.
Router
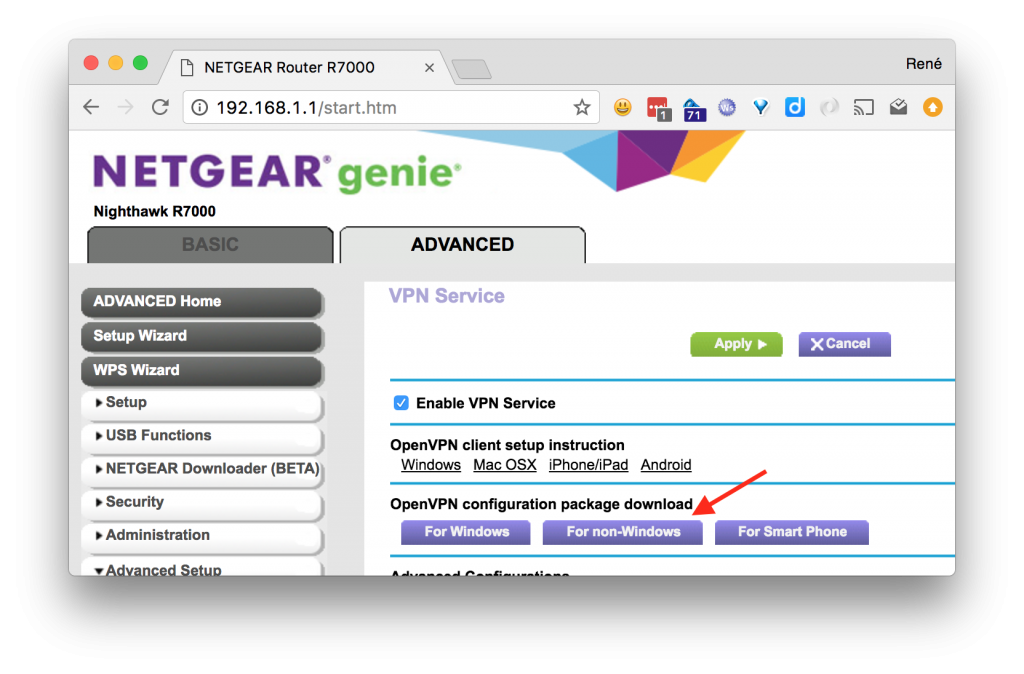
Start off by enabling the vpn service on the router, by going to ADVANCED > Advanced Setup > VPN Service, then check off Enable VPN Service and then click Apply.
When that is done and the router has rebooted, go back to the same page and download the VPN configuration zip file, nonwindows.zip, and copy it to the Pi:
rene $ scp nonwindows.zip pi@192.168.3.14: |
Pi
Log in to the Pi and set up OpenVPN:
rene $ ssh pi@192.168.3.14 pi:~$ sudo apt-get update && sudo apt-get install openvpn |
Once the installation is complete, add the configuration to openvpn:
pi:~$ unzip nonwindows.zip pi:~$ sudo cp client2.conf ca.crt client.crt client.key /etc/openvpn/ pi:~$ sudo chown root:root /etc/openvpn/{client2.conf,ca.crt,client.crt,client.key} pi:~$ sudo chmod 600 /etc/openvpn/{client2.conf,ca.crt,client.crt,client.key} pi:~$ ls -la /etc/openvpn/ total 28 drwxr-xr-x 2 root root 4096 Jul 13 14:13 . drwxr-xr-x 70 root root 4096 Jul 13 14:44 .. -rw------- 1 root root 1253 Jul 13 13:57 ca.crt -rw------- 1 root root 3576 Jul 13 13:57 client.crt -rw------- 1 root root 891 Jul 13 13:57 client.key -rw------- 1 root root 180 Jul 13 13:57 client2.conf -rwxr-xr-x 1 root root 1301 Nov 19 2015 update-resolv-conf |
Assuming you’re the only one accessing this Pi, setting the owner and file permissions isn’t strictly necessary, but nevertheless good practice. There’s no reason that these files should be readable by anyone but root.
Next you should edit /etc/default/openvpn and add a directive for the new configuration to start on boot:
AUTOSTART="client2" |
Now reboot the Pi and verify that a new network device has been added for the remote network:
pi:~$ ifconfig eth0 Link encap:Ethernet HWaddr b8:27:eb:1c:fa:81 inet addr:10.0.0.4 Bcast:10.0.0.255 Mask:255.255.255.0 UP BROADCAST RUNNING MULTICAST DYNAMIC MTU:1500 Metric:1 RX packets:4228 errors:0 dropped:0 overruns:0 frame:0 TX packets:1781 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:820993 (801.7 KiB) TX bytes:246368 (240.5 KiB) lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0 inet6 addr: ::1/128 Scope:Host UP LOOPBACK RUNNING MTU:65536 Metric:1 RX packets:13 errors:0 dropped:0 overruns:0 frame:0 TX packets:13 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1 RX bytes:1320 (1.2 KiB) TX bytes:1320 (1.2 KiB) tap0 Link encap:Ethernet HWaddr da:dd:3a:80:50:7c inet addr:192.168.1.7 Bcast:192.168.1.255 Mask:255.255.255.0 UP BROADCAST RUNNING MULTICAST DYNAMIC MTU:1500 Metric:1 RX packets:621 errors:0 dropped:0 overruns:0 frame:0 TX packets:177 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:100 RX bytes:70344 (68.6 KiB) TX bytes:15922 (15.5 KiB) |
Et voilà, that should be all there is to it!
Addendum
In case something didn’t quite go as planned, enabling some logging might be a good idea. Here’s a filtered list of options related to logging:
pi:~$ openvpn --help | grep log --topology t : Set --dev tun topology: 'net30', 'p2p', or 'subnet'. as the program name to the system logger. --syslog [name] : Output to syslog, but do not become a daemon. --log file : Output log to file which is created/truncated on open. --log-append file : Append log to file, or create file if nonexistent. --suppress-timestamps : Don't log timestamps to stdout/stderr. --echo [parms ...] : Echo parameters to log output. --management-log-cache n : Cache n lines of log file history for usage --mute-replay-warnings : Silence the output of replay warnings to log file. --pkcs11-cert-private [0|1] ... : Set if login should be performed before |
To make use of one of these options, it used to be, that the parameters could be passed in the OPTARGS directive of /etc/default/openvpn, but since OpenVPN has moved to using systemd, this is no longer supported. Relevant bug report.
Instead it is necessary to set them directly in each configuration. E.g. to enable append logging to a file add, edit /etc/openvpn/client2.conf and add the following line:
log-append /var/log/openvpn.log |
According the the man page verbosity is set from 0-11, and by default the vpn configuration from the R7000 has verbosity set to 5. This means the log file can quickly become rather large if left in append mode unattended, so make sure you have enough room on the SD card or remove the option again, when you are done debugging. Alternatively use –management-log-cache or truncate on each run by just using –log.
N.B. In my experience the client can be a bit flaky at times and I’ve often seen the first many connection attempts end in the following errors:
TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) TLS Error: TLS handshake failed |
And then after a number of tries, suddenly come through. Don’t ask me why.